Romulan has no specific knowledge of the BOI related events but has some experience in the area.
This is what happened
A BOI customer received a text, supposedly from BOI, followed the link and entered their account details including login and password.
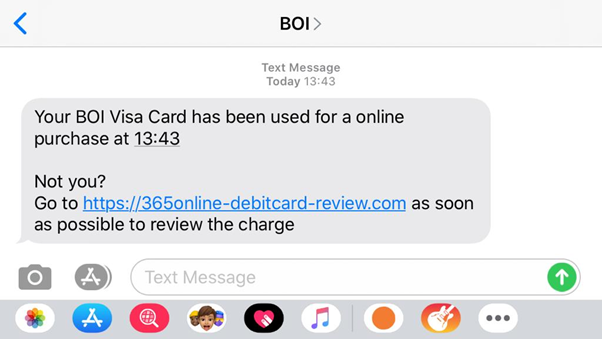
These allegations of what happened are incorrect
The texts came from Bank of Ireland…………No but they can be made to appear if they did in much the same way in emails.
The identity of the sender is spoofed in some way.
Try call back the number “BOI” above and it will look wrong.
“264” in this example.
Bank of Ireland systems were compromised by hackers…………No, It’s important to note that while they try to look as if they come from a reputable company, they do not, and it is highly unlikely that the IT systems of the reputable company have been compromised.
That said, there are occasions when data breaches occur, and data is obtained by the scammers and spammers.
This may allow a more targeted scam and spam attempt where they know something about you.
What BoI did wrong
I’ve yet to see an incident or problem that has not been made worse by poor communications.
BOI should have the means of detecting these events and protocols for responding.
Recognise the change from normal patterns of customer behaviour, tighten restrictions on systems where possible and communicate the issue immediately across all channels; radio, social media etc.
What the customers did wrong
They made a mistake, unfortunate to be sure.
If you look at the sample text, it’s not a bad effort but really, you should know the correct URL (address) of BOI online if you use it.
https://www.365online.com in this case.
If I had to pick one behaviour to change, I’d suggest don’t click on links in emails and texts without being very suspicious.
Don’t be hard on yourself afterwards, it happens and even Romulans get caught out on rare occasions.
What BoI could do to eliminate or reduce this happening again
A full report on the incident, analyse and learn the lessons.
Implement the changes required but know that it will happen again at some point.
Spammers and scammers will move on to other institutions and then return in due course.
BOI and other institutions do regularly flag this risk to customers
The problem is that you hear the warning so many times, you eventually cease to pay any attention to it.
What customers could do & Lessons to be learnt by customers
Spam texts are like spam emails, they want to pretend they are legitimate and come from a reputable company or organisation known to you.
Some are very poor and obvious, bad grammar and spelling mistakes everywhere.
Others try too hard and are easy to spot, the language for example may be very formal and excessive.
Then you get the ones in the middle, sometimes difficult to spot and especially when you start with a confirmation bias.
It’s not the scammers and spammers necessarily know anything about you, it’s a pure numbers game.
Send enough texts or emails and some are bound to generate a result.
What can you do to counter these scams and spams, be they email or text?
Well, start learning some good habits;
The scammers and spammers rely on a natural psychological need to DO SOMETHING.
It’s hard to learn, but DO NOTHING YET is a valid response.
This is what happened
A BOI customer received a text, supposedly from BOI, followed the link and entered their account details including login and password.
These allegations of what happened are incorrect
The texts came from Bank of Ireland…………No but they can be made to appear if they did in much the same way in emails.
The identity of the sender is spoofed in some way.
Try call back the number “BOI” above and it will look wrong.
“264” in this example.
Bank of Ireland systems were compromised by hackers…………No, It’s important to note that while they try to look as if they come from a reputable company, they do not, and it is highly unlikely that the IT systems of the reputable company have been compromised.
That said, there are occasions when data breaches occur, and data is obtained by the scammers and spammers.
This may allow a more targeted scam and spam attempt where they know something about you.
What BoI did wrong
I’ve yet to see an incident or problem that has not been made worse by poor communications.
BOI should have the means of detecting these events and protocols for responding.
Recognise the change from normal patterns of customer behaviour, tighten restrictions on systems where possible and communicate the issue immediately across all channels; radio, social media etc.
What the customers did wrong
They made a mistake, unfortunate to be sure.
If you look at the sample text, it’s not a bad effort but really, you should know the correct URL (address) of BOI online if you use it.
https://www.365online.com in this case.
If I had to pick one behaviour to change, I’d suggest don’t click on links in emails and texts without being very suspicious.
Don’t be hard on yourself afterwards, it happens and even Romulans get caught out on rare occasions.
What BoI could do to eliminate or reduce this happening again
A full report on the incident, analyse and learn the lessons.
Implement the changes required but know that it will happen again at some point.
Spammers and scammers will move on to other institutions and then return in due course.
BOI and other institutions do regularly flag this risk to customers
The problem is that you hear the warning so many times, you eventually cease to pay any attention to it.
What customers could do & Lessons to be learnt by customers
Spam texts are like spam emails, they want to pretend they are legitimate and come from a reputable company or organisation known to you.
Some are very poor and obvious, bad grammar and spelling mistakes everywhere.
Others try too hard and are easy to spot, the language for example may be very formal and excessive.
Then you get the ones in the middle, sometimes difficult to spot and especially when you start with a confirmation bias.
- You normally deal with, say PAYPAL, so contact from them is not surprising
- You are expecting a parcel from say, DPD, and suddenly an email arrives requesting a redelivery charge
- Your bank is, say BOI, and they have your mobile on record and you receive a text
It’s not the scammers and spammers necessarily know anything about you, it’s a pure numbers game.
Send enough texts or emails and some are bound to generate a result.
What can you do to counter these scams and spams, be they email or text?
Well, start learning some good habits;
- Never click on a URL link in an email or text. You should either know them or have them saved in your browser favourites
- Emails that do not address you by name are high risk, think about it, Paypal should know your name
- Use your cursor to hover over a FROM email address or URL link if possible, take a look at what the underlying link is and not what is displayed
- The IE domain is a managed domain so emails and links with a .IE in them are more trustworthy than those with a .COM as a general rule
- Do not ring any number listed in the email or text. Double check the number elsewhere and then ring if necessary
- Have the emergency numbers for cancelling cards to hand or better still, know how to cancel then from the relevant APP..............If in doubt, cancel immediately, don’t hesitate. It’s a pain, but you can get another card relatively quickly.
The scammers and spammers rely on a natural psychological need to DO SOMETHING.
It’s hard to learn, but DO NOTHING YET is a valid response.